Distance Vector Routing
Distance Vector Routing trendy pc networks typically use dynamic routing algorithms instead of the static ones delineated higher than. Two dynamic algorithms above all, Orcus tance vector routing and link state routing, ar the foremost standard. In this section we will look at fermer algorithm. In the following one we will study the latter one. Distance vector routing algorithms operate by having each router maintain a table (i.e, a vector) giving the best known distance to each destination and which line to use to get there. These tables ar updated by exchanging info with the neighbors. The distance vector routing rule is often referred to as by totally different names, including the distributed Bellman-Ford routing algorithm and the Ford Fulkerson algorithm, after the researchers who developed it (Bellman, 1957; and Ford and Fulkerson, 1962). It was the initial ARPANET routing rule and was conjointly employed in the web beneath the name RIP and in early versions of DECnet and Novell’s IPX. AppleTalk and Cisco routers use improved distance vector protocols. In distance vector routing, each router maintains a routing table indexed by, and containing one entry for, each router in the subnet. This entry contains a pair of parts: the favored outgoing line to use for that destination, and an estimate of the time or distance to that destination. The metric used may well be range of hops, time delay in milliseconds, total number of packets queued along the path, or something similar. The router is assumed to grasp the “distance” to every of its neighbors. If the metric is hops, the space is simply one hop. If the metric is queue length, the router merely examines every queue.
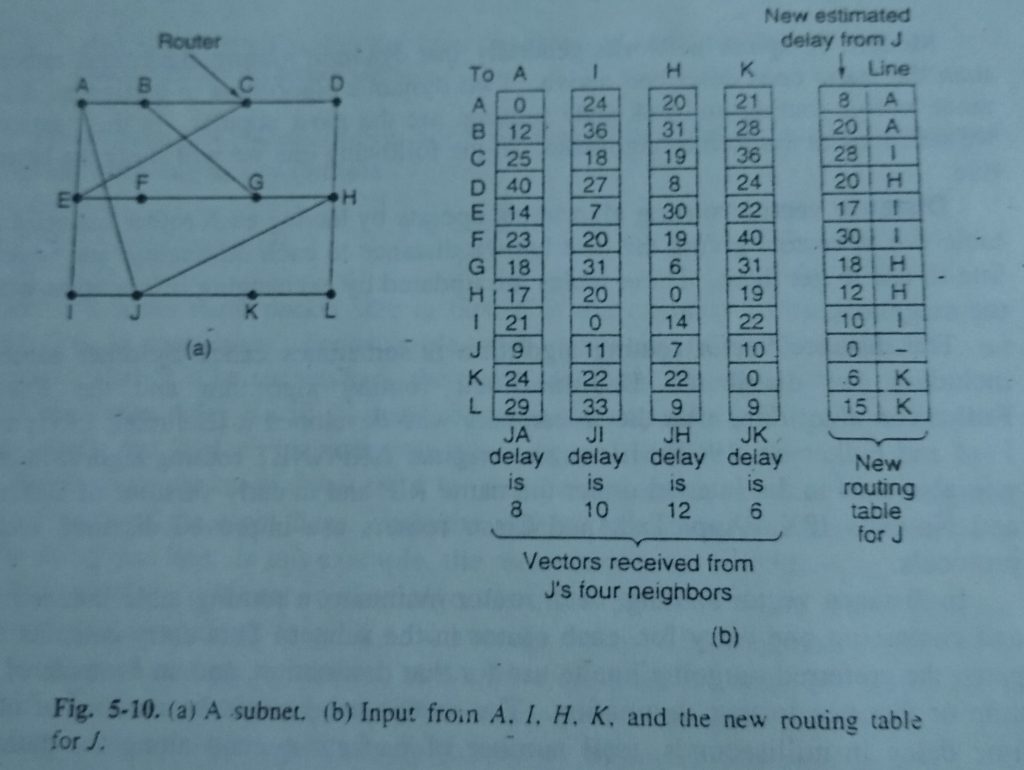
If the metric is delay, the router will live it directly with special ECHO packets that the receiver simply timestamps and sends back as quick because it will. As Associate in Nursing example,(Distance Vector Routing) assume that delay is used as a metric and that the router knows the delay to each of its neighbors. Once each T time unit every router sends to every neighbor a listing of its calculable delays to every destination. It conjointly receives an identical list from every neighbor. Imagine that one of these tables has just come in from neighbor X, with X; being X’s estimate of how long it takes to get to router t. If the router is aware of that the delay to X is m time unit, it also knows that it can reach router i via X in X; + m msec via X. By performing arts this calculation for every neighbor, a router can find out which estimate seems the best and use that esti mate and the corresponding line in its new routing table. Note that the recent routing table isn’t employed in the calculation. This updating process is illustrated in Fig. 5-10. Part (a) shows a subnet. The first four columns of pant (b) show the delay vectors received from the neighbors of router JA ciaims to have a 12-msec delay to B, a 25-msec delay to C, a forty time unit delay to D. etc. Suppose that has measured or estimated its delay to its neighbors, A, I. H. and K as 8. 10, 12, and 6 msec, respectively.
Consider how computes its new route to router G.(Distance Vector Routing) It knows that it can get to A in eight millisecond, and A claims to be able to get to G in 18 msec, so J knows it can count on a delay of twenty six millisecond to G if it forwards packets certain for G to A. Similarly, it computes the delay to G via one, H, and K as forty one (31 + 10), 18 (6 + 12 and 37 (31 + 6) msec respectively. The best of those values is eighteen, thus it makes entry in its routing table that the delay to G is eighteen millisecond, and that the route to use via H. The same calculation is performed for all the opposite destinations, with new routing table shown within the last column of the figure.
The Count-to-Infinity Problem
Distance vector routing works in theory however encompasses a serious disadvantage in pr tice: though it converges to the right answer, it should do therefore slowly. In part lar, it reacts rapidly to good news, but leisurely to bad news. Consider a ro whose best route to destination X is large. If on the next exchange neighbor suddenly reports a brief delay to X, the router simply switches over to exploitation the to A to send traffic to X. In one vector exchange, the nice news is processed. To see how briskly excellent news propagates, consider the five-node (linear) subnet of Fig. 5-11, wherever the delay metric is that the range of hops. Suppose A is down initially and all the other routers know this. In other words, they have all recorded the delay to A as infinity.
When A comes up, the opposite routers find out about it via the vector exchanges For Simplicity we are going to assume that there’s a big gong somewhere that’s smitten sporadically to initiate a vector exchange in the least routers at the same time. At the time of the primary exchange, B learns that its left neighbor has zero delay to A. B currently makes associate degree entry in its routing table that A is one hop away to the left. All the opposite routers still suppose that A is down. At now, the routing table entries for A ar as shown within the second row of Fig. 5-11(a). On successive exchange, C learns that B includes a path of length one to A, so it updates its routing table to indicate a path of length 2, but D and E don’t hear the great news till later. Clearly, the good news is spreading ai the rate of one hop per exchange. In a subnet whose longest path is of length N hops, at intervals N exchanges everybody can fathom recently revived lines and routers. Now let us consider the situation of Fig. 5-11(b), within which all the lines and routers ar ab initio up. Routers B, C, D, and E have distances to A of one, 2, 3, and 4, severally.
Suddenly A goes down, or or else, the line between A and B is cut, which is effectively the same thing from B’s point of view. At the primary packet exchange, B doesn’t hear something from A. Fortunately, C says “Do not worry. I have a path to A of length two.” very little will B understand that C’s path runs through B itself. For all B is aware of, C might have ten outgoing lines all with independent paths to A of length 2. As a result, 3 now thinks it can reach A via C, with a path length of 3. D and E don’t update their entries for A on the primary exchange. On the second exchange, C notices that every of its neighbors claims to possess a path to A of length three. It picks one of the them at random and makes its new dis tance to A 4, as shown in the third row of Fig. 5-11(b). Subsequent exchanges manufacture the history shown within the remainder of Fig. 5-11(b). From this figure, its ought to be clear why dangerous news travels slowly: no router ever includes a price quite one on top of the minimum of all its neighbors. Gradually, all the routers work their far to time, but the number of exchanges required depends on the numerical value used for infinity. For this reason, it is wise to set infinity to the longest path plus 1. If the metric is time delay, here is no well-defined upper bound, so a high value is needed to prevent a path with a long delay from being treated as down. Not entirely astonishingly, this drawback is understood because the count-to-infinity drawback.
The Split Horizon Hack
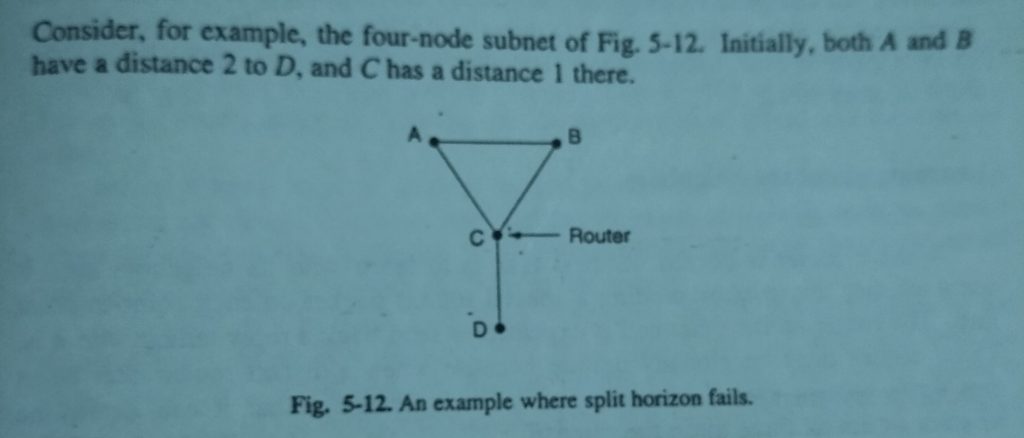
Many impromptu solutions to the count-to time downside are planned within the literature, all a lot of sophisticated and fewer helpful than the one before it we are going to describe just one of them here so tell why it, too, fails. The split horizon formula works identical method as distance vector routing, except that the distance to X is not reported on the line that packets for X are sent on (actually, it is reported as infinity). In the initial state of Fig. 5-11(b), for example, C tells D the truth about the distance to A,(Distance Vector Routing) but C tells B that its distance to A is infinite. Similarly, D tells the reality to E however lies to C. Now let us see what happens when A goes down. On the primary exchange, B discovers that the direct line is gone, and C is reporting an infinite distance to A as well. Since neither of its neighbors will get to A. B sets its distance to infinity as well. On consecutive exchange, C hears that A is unreachable from both of its neighbors, so it marks A as unreachable too. Using split horizon, the bad news propagates one hop per exchange. This rate is far higher than while not split horizon. The real unhealthy news is that split horizon, though wide used, typically fails.
Now suppose that the CD line goes down. Using split horizon, each A and B tell C that they can not get to D. Thus C straightaway concludes that D is unreach ready and reports this to each A and B. Unfortunately, A hears that B features a path of length two to D, thus it assumes it will get to D via B in three hops. Similarly, B concludes it will get to D via A in three hops. On future exchange, they every set their distance to D to four. Both of them step by step count to eternity, exactly the behavior we tend to were making an attempt to avoid.
 PollyBD Networking Blogspot
PollyBD Networking Blogspot