Distributing the Link State Packets
Distributing the Link State Packets The trickiest piece of the calculation is conveying the connection state bundles reliably.As the parcels are circulated and introduced, the switches getting the initial ones will change their courses Consequently, the various switches might be utilizing various variants of the topology, which can prompt irregularities, circles, inaccessible machines. what’s more, different issues. first we will portray the essential conveyance calculation. Later we will give a few refinements. the principal thought is to utilize flooding to circulate the connection state parcels. To hold the flood under wraps , every bundle contains an arrangement number that is increased for each new parcel sent. Switches monitor all the(source switch, sequence)pairs they see. at the point when another connection state parcel comes in it is chec ked against the rundown of bundles as of now seen.lf it is new,it is sent on all lines aside from the one it landed on If it is a copy. it is disposed of. On the off chance that a bundle with an arrangement number lower than the most noteworthy one seen so far ever shows up, it is dismissed as being out of date. This calculation has a couple of issues, however they are reasonable. to begin with, if the arrangement numbers fold over, disarray will reign.the arrangement here is to utilize a 32-piece grouping number.with one connection state bundle for every second,it would take 137 years to fold over, so this probability can be overlooked. Second, if a switch ever crashes, it will forget about its succession number. On the off chance that it begins again at O, the following paccket will be dismissed as a copy.
Third if a succession number is ever defiled and 65,540 is gotten rather than 4(a l-bit error)(Distributing the Link State Packets),packets 5 through 65,540 will be dismissed as old, since the present grouping number is believed to be 65,540. The answer for every one of these issues is to incorporate the age of every bundle after the arrangement number and decrement it once every second. at the point when the age hits zero, the data from that ronter is disposed of. Typically another parcel comes in, say,every 10 minutes,so switch data possibly times out when a switch is down (or six back to back bundles have been lost,an far-fetched occasion). The age field is aiso decremented by every switch during theinitial flooding process,to ensure no parcel can get lost and live for an uncertain timeframe (a bundle whose age is zero is discarded).Some refinements to this calculation make it increasingly powerful. At the point when a connection state bundle comes in to a routerfor flooding, it isn’t lined for transmission immediately.Instead it is placed in a holding territory to hold up a brief time first. lf another connection state bundle from a similar source comes in before it is transmitted their grouping numbers are thought about. lf they are equal,the copy is discarded,if they are distinctive the more established one is tossed out. To make preparations for mistakes on the switch lines, all connection state bundles are acknowledged.when a line goes inert, the holding territory is filtered in cooperative request to choose a parcel or affirmation to send.
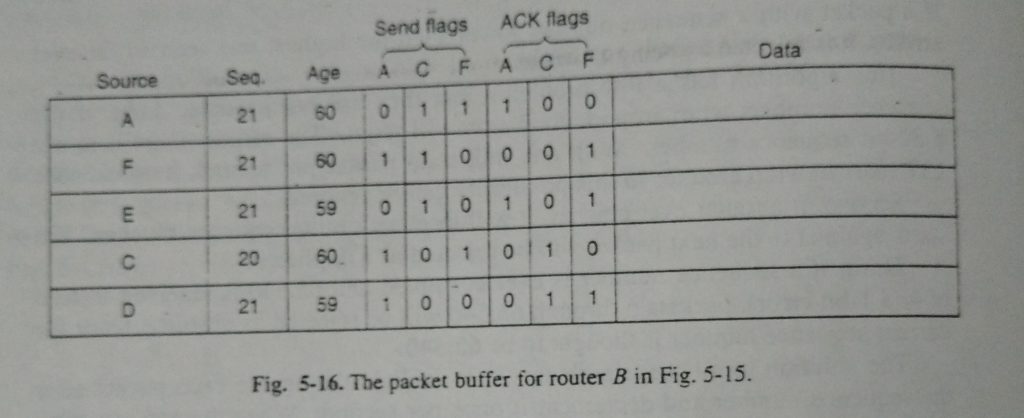
The information structure utilized by switch B for the subnet appeared in is Depicted in Fig. 5-16. Each tow here relates to an as of late showed up, yet so far ocessed,(Distributing the Link State Packets) interface state bundle. The table records where the parcel started, its arrangement number and age, and the information. What’s more, there are send and affirmation banners for every one of B’s three lines (to A, C, and F, individually). The send banners imply that the bundle must be sent on the demonstrated line. The affirmation banners imply that it must be recognized there. In Fig. 5-16, the connection state parcel from A showed up legitimately, so it must be sent to C and F and recognized to An, as demonstrated by the banner bits. “Correspondingly, the bundle from F must be sent to An and C and recognized to F. In any case, the circumstance with the third parcel, irom E, is extraordinary. It showed up twice, once through EAB and once by means of EFB. Thus, it must be sent distinctly to C. be that as it may, recognized to both An and F, as demonstrated by the bits. In the event that a copy shows up while the first is still in the support, bits must be changed. For instance, if a duplicate of C’s state lands from F before the fourth
entry in the table has been forwarded, the six bits will be changed to 100011 to indicate that the packet must be acknowledged to F but not sent there.
Computing the New Routes
When a switch has gathered a full arrangement of connection state parcels, it can develop the whole subnet diagram in light of the fact that each connection is spoken to. Each connection is, indeed, spoken to twice, once for every bearing. The two qualities can be found the middle value of or utilized independently. Presently Dijkstra’s calculation can be run locally to build the most limited way to every conceivable goal. The aftereffects of this calculation can be introduced in the defeat ing tables, and typical activity continued. For a subnet with n switches, every one of which has k neighbors, the memory required to store the info information is corresponding to kn. For huge subnets, this can be an issue. Additionally, the calculation time can be an issue. In any case, in numerous pragmatic circumstances, connect state directing functions admirably. Nonetheless, issues with the equipment or programming can unleash devastation with this calculation (likewise with different ones). For instance, if a switch professes to have a line it doesn’t have, or overlooks a line it has, the subnet diagram will be off base. In the event that a switch neglects to advance bundles, or ruins them while sending them. inconvenience wil emerge. At last, on the off chance that it comes up short on memory or does the directing computation off-base, terrible things will occur.
As he subnet develops into the scope of tens or a huge number of hubs. the likelihood of some switch bombing at times gets nonnegligible. Try to attempt to mastermind to constrain the harm when the inevit abie occurs. Periman (1988) examines these issues and their answers in detail Link state steering is broadly utilized in genuine systems. so a couple of words about some model conventions utilizing it are all together. The OSPF convention, which is progressively being utilized in the Internet, utilizes a connection state calculation. We will depict OSPF in Sec. 5.5.5. Another significant connection state convention IS-IS (Intermediate System Intermediate System), which was intended for DECnet and later embraced by ISO for use with its connectionless system layer convention, CLNP. From that point forward it has been changed to deal with different conventions too, most quite, IP. Is utilized in various Internet spines (counting the old NSFNET spine), and in some computerized cell frameworks, for example, CDPD. Novell NetWare utilizes a minor variation of IS-IS (NLSP) for steering IPX bundles. Fundamentally IS-IS disperses an image of the switch topology, from which the most limited ways are figured.
Every switch reports, in its connection state data, which system layer tends to it can reach straightforwardly. These addresses can be IP, IPX, AppleTalk, or some other locations. IS-IS can even help various system layer conventions simultaneously. A significant number of the developments intended for IS-IS were embraced by (OSPF was planned quite a long while after IS-IS). These incorporate a self-settling strategy for flooding join state refreshes, the idea of an assigned switch on a LAN, and the technique for registering and supporting way parting and various measurements. As a result, there is almost no distinction between IS-IS and OSPF. The most significant distinction is that is encoded so that it is simple and regular to all the while convey data about different system layer conventions, a component OSPF doesn’t have. This favorable position is particularly significant in huge multiprotocol situations.
HOME PollyBD Networking Blogspot
PollyBD Networking Blogspot